Understanding the Fundamentals
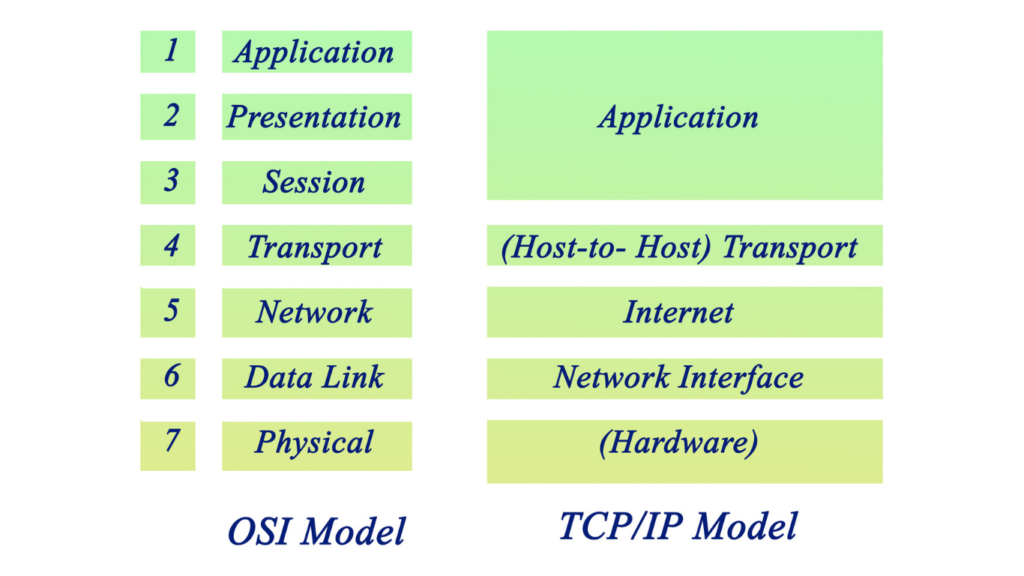
The OSI (Open Systems Interconnection) Model:
In every networking class, the OSI Model takes centre stage, offering a comprehensive framework to explore the intricacies of communication between two computer devices. When embarking on setting up a network between two computers, the initial consideration revolves around connecting them. This process involves selecting a medium, be it copper cabling, glass tubes, or radio waves. Each medium comes with its set of considerations, necessitating a deep understanding of how to use them to transmit meaningful information. This initial step falls under Layer 1, known as the Physical layer, where information is fundamentally encoded into bits (1s and 0s).
Progressing to Layer 2, or the Data Link layer, one encounters considerations about network expansion. The decision to allow more than two nodes to join brings addressing to the forefront. Layer 2 efficiently manages this aspect by utilizing frames to encapsulate data from higher layers, holding addresses that identify machines within a specific network.
Expanding Beyond: Layer 3, the Network layer, intervenes as networks grow, introducing packets that contain vital network addresses and routing information. This layer is pivotal for sending messages to other neighbourhoods or even cities, ensuring that routers along the way understand the intended destination of the message.
Scaling Up: As networks expand, Layer 4, the Transport layer, assumes a crucial role. It addresses issues of reliable delivery and flow control, managing end-to-end delivery, error correction through retransmission, and flow control. This layer ensures that messages are not only delivered accurately but also without overwhelming the network.
Navigating the Data Layers: Moving up the stack, Layers 5 to 7 (Session, Presentation, and Application) concentrate on the data itself. The Session layer opens, maintains, and closes sessions; the Presentation layer ensures messages are universally understandable, while the Application layer holds protocols for user access to information across the network. These three layers, collectively referred to as the “data layers,” align directly with the Application layer of the TCP/IP stack.
In conclusion, from establishing a communication medium to addressing, routing, and ensuring reliable delivery, each layer in the networking stack plays a pivotal role in constructing a functional and efficient network.

The TCP/IP (Transmission Control Protocol/Internet Protocol) Model
While both the OSI model and the TCP/IP model serve as conceptual frameworks defining the functions and interactions in computer networking, they were independently developed with slightly different purposes. The TCP/IP model traces its origins to the early ARPANET, seeking to establish a robust and universal communication protocol. Over the years, TCP/IP has evolved into the standard for network communication, laying the foundation for our interconnected world today.
Breaking Down the Layers:
Link Layer (Network Interface Layer):
At the foundation of the TCP/IP model lies the Link Layer, responsible for the physical connection between devices on the same network. It deals with hardware aspects, specifying how data is framed and transmitted over various physical mediums like Ethernet or Wi-Fi.
Internet Layer:
Sitting atop the Link Layer, the Internet Layer manages addressing and routing between networks. The Internet Protocol (IP) is a cornerstone, assigning unique addresses and ensuring data packets reach their intended destinations.
Transport Layer:
Progressing up the hierarchy, the Transport Layer focuses on end-to-end communication. Protocols like TCP and UDP come into play, ensuring reliable and ordered data delivery.
Application Layer:
At the topmost layer is the Application Layer, where user interactions occur. This layer encompasses various protocols for specific applications, such as HTTP, SMTP, and FTP.
In essence, the TCP/IP model encapsulates the essence of modern network communication, providing a structured framework for understanding and implementing effective networking solutions.
