Key Topics Every Aspiring Ethical Hacker Must Conquer in Networking Part 3 – Ref: E3

Navigating the Basics: A Simplified Journey through Network Communication
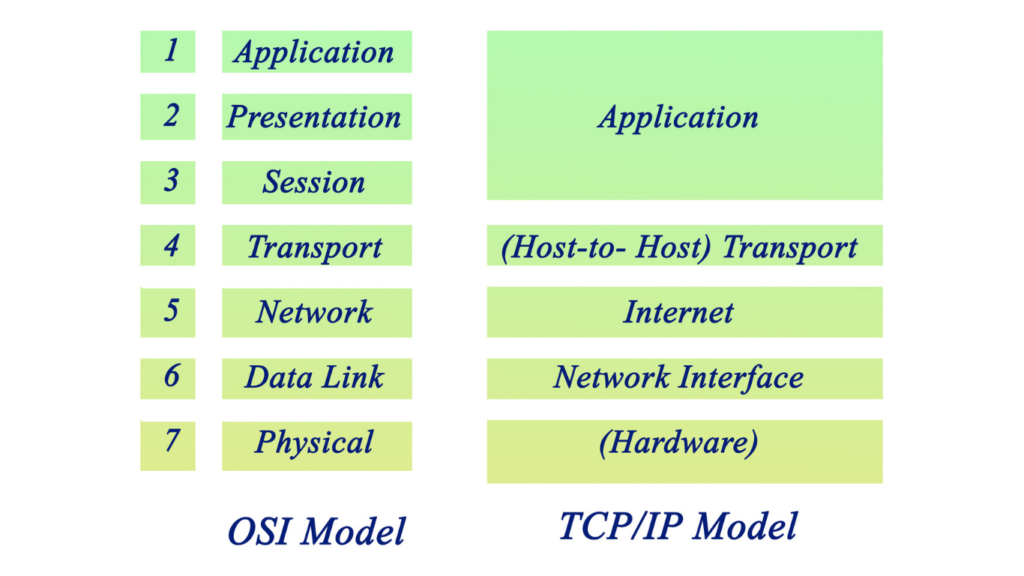
In this scenario, let’s explore the journey of a message travelling from one machine to another within a TCP/IP network. Picture user Peter, eager to browse online for products at Hay Supermarket. Upon opening his browser and requesting his favourite shop’s website, Peter’s computer realizes it can’t locate the requested page locally in its cache memory. To find the information, it searches for a network entity to respond. Opting for the HTTP protocol (port 80), initiates the creation of a session—segments of data exchanged to accomplish a specific goal.
Within the framework of an Ethernet TCP/IP network, akin to Peter’s setup, communication between computers occurs through bits arranged in specific order, termed frames. These frames are constructed from the inside out, drawing on information from the upper layers. For example, the Application layer passes down an HTTP request to the Transport layer. Recognizing the need for a reliable, connection-oriented session, Peter’s computer turns to the Transmission Control Protocol (TCP). TCP kickstarts a three-step handshake (SYN, SYN/ACK, ACK) to establish a communication session with the destination.
Essentially, Peter’s computer embarks on a series of messages to forge a dependable connection, ensuring that Peter receives the desired information without any loss. This simplified narrative is designed to cover the foundational aspects without delving too deeply into technical intricacies, providing a clear understanding of the essential concepts involved in network communication.
Key Topics Every Aspiring Ethical Hacker Must Conquer in Networking Part 3 – Ref: E3 Read More »