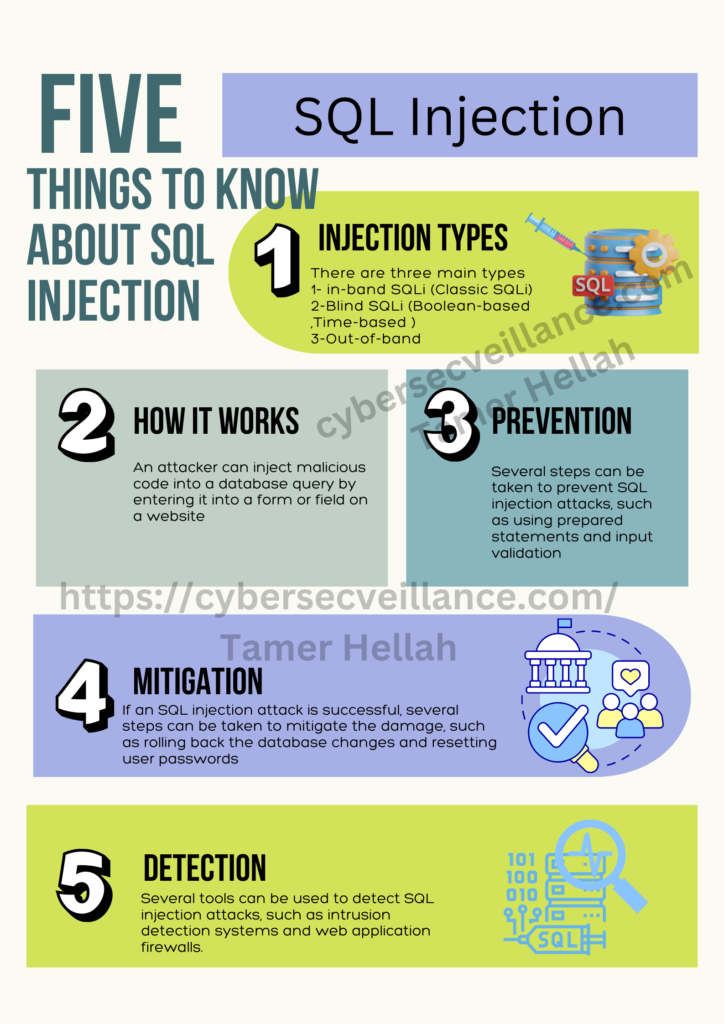
Understanding Active Directory Authentication and Security
1. Active Directory (AD) Authentication
Active Directory (AD) Authentication is a Windows-based system that manages who can access the network (authentication) and what they can do once they are in (authorization).
Centralized Management: AD provides centralized control over user and device settings, and streamlines user and rights management using Group Policy.
Single Sign-On (SSO): With AD, users log in once and then can access all authorized resources within the network without needing to log in again.
2. Authentication Protocols
Kerberos Protocol:
- Secure Logins: Users log in once and get a “ticket” instead of sending passwords over the network.
- Key Distribution Center (KDC): It has two parts – an Authentication Server (AS) and a Ticket Granting Server (TGS). The AS verifies the user and gives them a Ticket Granting Ticket (TGT). The user then uses the TGT to get access tokens from the TGS to access different services.
- Session Keys: These are temporary keys used for the session to keep communication secure.
Lightweight Directory Access Protocol (LDAP):
- Open-Source Protocol: It allows AD to provide authentication services.
- Simple Authentication: Uses basic login credentials.
- SASL (Simple Authentication and Security Layer): Uses other authentication methods like Kerberos for added security.
3. Older and Less Secure Protocols
LAN Manager (LM) Hash:
- Weak Security: It splits passwords into two 7-character chunks and hashes them separately, making it easier to crack.
- Outdated: Modern systems don’t use LM by default but might still be present in old systems.
NT LAN Manager (NTLM) Hash:
- Improved Security: Supports longer passwords and is case-sensitive.
- Pass-the-Hash Attack: Attackers can use the hash to impersonate the user without knowing the actual password.
NTLMv1 and NTLMv2:
- Challenge-Response Mechanism: The server sends a challenge, and the client responds with an encrypted version of the challenge.
- NTLMv2: More secure with added client challenge and server timestamp but still less secure than Kerberos.
4. AD Domain Users and the KRBTGT Account
Domain Users:
- Access Resources: Domain users can access shared resources like file servers and printers.
- Log in Anywhere: They can log in to any computer within the domain.
KRBTGT Account:
- Special Account: It’s crucial for the Kerberos authentication process.
- Target for Attackers: If compromised, it can be used to create “Golden Tickets” that give attackers unlimited access.
5. Golden Ticket Attack
Step-by-Step Attack:
- Initial Compromise: Attackers get into the network, often using phishing.
- Privilege Escalation: They gain higher access, targeting admin accounts.
- Extract KRBTGT Hash: Using tools, they extract the hash from the AD database.
- Create Golden Tickets: With the KRBTGT hash, they forge tickets that give them unrestricted access to the domain.
6. Local Accounts
Types of Local Accounts:
- Administrator: Has full control over the system.
- Guest: Disabled by default, provides temporary access.
- SYSTEM: Used by the OS for internal functions.
- Network Service: Used by services that need to access network resources.
- Local Service: Used by services that need minimal privileges.
Summary
- Authentication: Verifies who you are.
- Authorization: Determines what you can do.
- Access Control: Manages permissions.
- Users: Individuals with access to the network.
- KRBTGT: Key account in Kerberos authentication.
- Golden Ticket Attack: A major security threat that exploits the KRBTGT account to gain full domain access.
By understanding these elements, you can better grasp how Active Directory helps secure a Windows-based network and why it’s crucial to protect against specific threats like the Golden Ticket attack.
Understanding Active Directory Authentication and Security Read More »