Exploring the vast landscape of cloud environments like Azure often involves navigating intricate relationships and potential attack paths. Recently, while attempting to utilize BloodHound and the AzureHound collector to assess an Azure environment’s vulnerabilities, an unexpected hurdle emerged, requiring a deeper dive into troubleshooting and resolution.
In an effort to execute this assessment, the initial step necessitated the provision of the target Azure tenant ID. This crucial identifier could be obtained by logging into the Azure CLI via ‘az login’. However, operating from a Kali Linux environment, the journey was met with complexities that demanded meticulous problem-solving.

Executing ‘az login’ in the PowerShell environment after accessing it via ‘pwsh’ in the Kali machine should have initiated the process smoothly. Yet, the attempt to proceed with ‘Connect-AzureAD’ for user authentication led to a frustrating series of errors, culminating in the message: “Connect-AzureAD: The term ‘Connect-AzureAD’ is not recognized as a name of a cmdlet, function, script file, or executable program.”
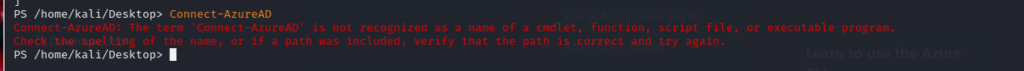
This error is a common manifestation when the necessary ‘Connect-AzureAD’ cmdlet, integral to the Azure Active Directory PowerShell module, is absent or improperly installed within the PowerShell environment. The resolution path was illuminated by considering several potential causes and their corresponding solutions.
Primarily, the absence of the Azure Active Directory PowerShell module stood out as a probable culprit. To rectify this, an attempt to install the module from the PowerShell Gallery was made. The process involved executing ‘Install-Module -Name Az -AllowClobber -Scope CurrentUser’ in PowerShell as an administrator, yet this did not resolve the issue.
Further investigation suggested the possibility of version inconsistencies or update issues within the AzureAD module. Consequently, an attempt to update the module using ‘Update-Module -Name Az’ was made, but the error persisted.
A consideration that couldn’t be overlooked was the PowerShell execution policy, which, if restrictive, might impede the loading of the AzureAD module. Temporarily adjusting the execution policy using ‘Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass’ was attempted but did not yield the anticipated result.
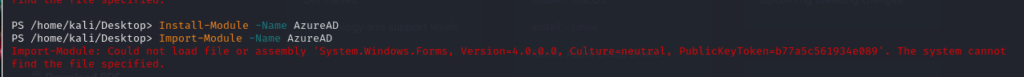
A critical discovery was made upon scrutinizing documentation related to the AzureAD module, which indicated its deprecated status. This revelation aligned with the persistent connectivity issues encountered while attempting to extract object IDs through Microsoft Graph.
Despite efforts to troubleshoot and explore various avenues, the desired outcome remained elusive. I hold the belief that the Microsoft Graph output lacked the required level of granularity., providing object IDs instead of user, group, or service principal names, complicating the assessment further.
In conclusion, the journey to assess Azure environment vulnerabilities using BloodHound and AzureHound encountered roadblocks due to connectivity issues, deprecated modules, and output limitations. Addressing these challenges demands innovative solutions or alternative approaches to achieve comprehensive and accurate assessments.
